GRTech
Sophos Launches Industry-First Managed Detection and Response (MDR) Service from an Endpoint Security Provider
Sophos X-Ops Identifies LockBit 3.0 Similarities to BlackMatter; Attackers Use Pentesting and Credential Theft to Evade Detection, Requiring Specialized MDR Skills to Spot Them
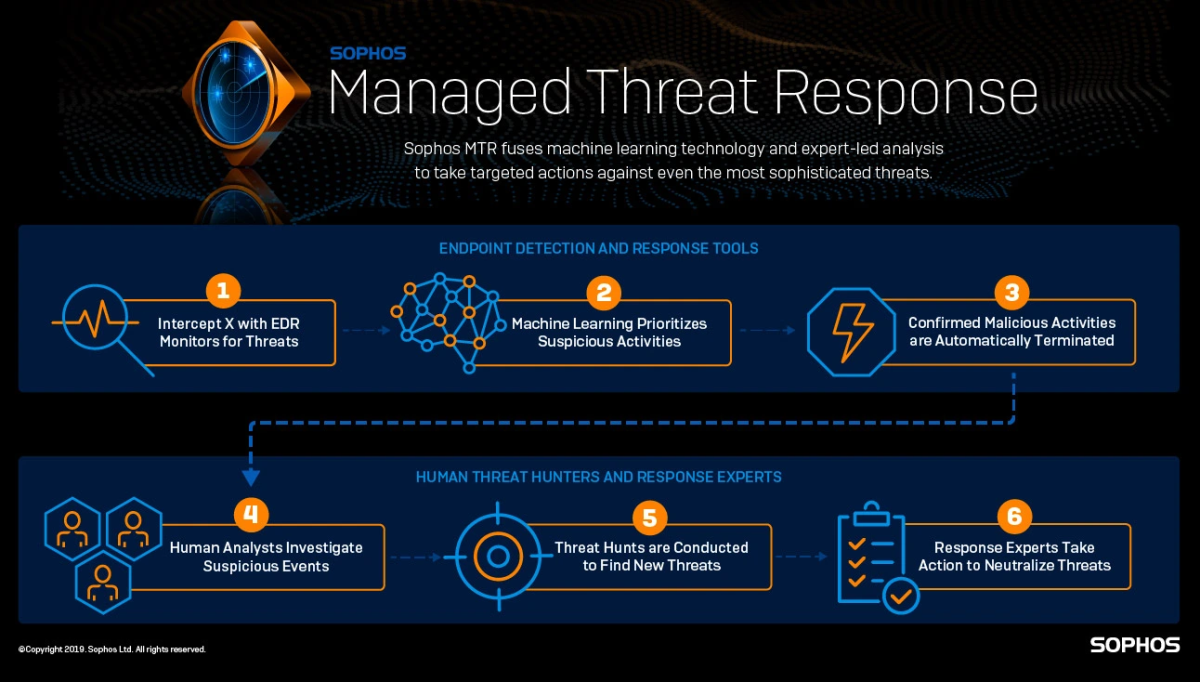

Sophos, a global leader in innovating and delivering cybersecurity as a service, has announced the general availability of Sophos Managed Detection and Response (MDR) with new industry-first threat detection and response capabilities.
Sophos is the first endpoint security provider to integrate vendor agnostic telemetry from third-party security technologies into its MDR offering, providing unprecedented visibility and detection across diverse operating environments. Sophos also introduced the Sophos Marketplace and $1 million Sophos Breach Protection Warranty.
The need for MDR services and specialized defenders has never been greater, as shown in today’s new research, “LockBit 3.0 ‘Black’ Attacks and Leaks Reveal Wormable Capabilities and Tooling,” from Sophos X-Ops, the company’s cross-domain threat intelligence unit. The research analyzes tactics, techniques and procedures (TTPs) used by LockBit, one of today’s most prolific ransomware gangs, that are similar to BlackMatter, and explains how the latest version of the ransomware, LockBit 3.0, adds wormable capabilities and uses legitimate pentesting tools to evade detection.
In a second article, “Detection Tools and Human Analysis Lead to a Security Non-Event,” Sophos X-Ops details a recent Sophos MDR use case involving credential theft, another technique that allows adversaries to impersonate legitimate users. In this case, the Sophos MDR team combined its threat hunting intelligence with information from the customer’s third-party security appliance to thwart an attack.
“The only way to reliably detect and neutralize determined attackers who increasingly combine the use of pentesting tools, stolen credentials and other stealthy tactics to maneuver undetected is with 24×7 eyes on glass, operating on signals from a diversity of event sources and employing actionable threat intelligence into real-time attacker behaviors,” said Joe Levy, chief technology and product officer at Sophos. “Organizations are struggling to keep pace with well-funded adversaries who are continuously innovating and industrializing their ability to evade defensive technologies alone. Sophos MDR can discover and intercept these steps before they result in a data breach, ransomware or other type of costly compromise. Sadly, ransomware persists as one of the greatest cybercrime threats to organizations, as evidenced in the Sophos 2023 Threat Report. We’re raising the industry standard for how critical MDR services can be delivered to broaden visibility for better, faster detection and response.”
Industry-First Detection and Response and the New Sophos Marketplace
Sophos is the first leading endpoint security provider delivering MDR across both its own product portfolio as well as end users’ existing security deployments. To support this effort, Sophos launched the Sophos Marketplace, an open ecosystem of more than 75 technology integrations, including Amazon Web Services (AWS), Check Point, CrowdStrike, Darktrace, Fortinet, Google, Microsoft, Okta, Palo Alto Networks, Rapid7, and many others. Expanded visibility across these integrations and diverse operating environments enables Sophos MDR experts to better detect and remediate attacks with speed and precision, regardless of customers’ existing security solutions.
In addition to Sophos MDR, Sophos Marketplace provides third-party integrations for Sophos’ portfolio of services, products and technologies. Telemetry is automatically consolidated, correlated and prioritized with insights from the Sophos Adaptive Cybersecurity Ecosystem and the Sophos X-Ops threat intelligence unit.
Extended Protection Warranty
Sophos stands behind its MDR customers with the new Sophos Breach Protection Warranty that covers up to $1 million in response expenses for organizations protected by Sophos MDR Complete, Sophos’ most comprehensive MDR offering. Underwritten solely by Sophos, the warranty covers endpoints – both Windows and Mac devices – and servers, and unlike competitive offerings, there are no warranty tiers or duration limitations for active customers. This Sophos Breach Protection Warranty is automatically included with all purchases and renewals of Sophos MDR Complete annual subscriptions through Sophos’ global reseller partner network.
Availability
More than 13,000 organizations already rely on Sophos’ existing MDR service for 24/7 threat hunting, detection and response by an expert team as a fully-managed service. The newest offering with third party integration capabilities is available now, and the service is customizable with different tiers and threat response options, enabling customers to choose whether to have the Sophos MDR operations team execute full-scale incident response, provide collaborative assistance for confirmed threats, or deliver detailed alert notifications for their security operations teams to manage themselves.
-



 News4 days ago
News4 days ago‘You escape, or you die’: African men say Russia duped them into fighting in Ukraine
-



 Hospitality2 days ago
Hospitality2 days agoThe Nature Conservancy and FSC Africa Sign Strategic Partnership to Strengthen Sustainable Forest Management Across Africa
-



 Transport2 days ago
Transport2 days agoAkin Fadeyi Foundation unveils new advocacy campaign to curb road accidents
-



 Energy2 days ago
Energy2 days agoPayment Security Remains Biggest Barrier to Bankable Gas and Power Projects — FirstCap MD






