TechNews
Sophos’ Active Adversary Playbook 2022 Reveals Attacker Dwell Time Increased by 36%
Increase attributed to exploitation of ProxyLogon and ProxyShell vulnerabilities, plus initial access brokers


Sophos, a global leader in next-generation cybersecurity, today released the “Active Adversary Playbook 2022,” detailing attacker behaviors that Sophos’ Rapid Response team saw in the wild in 2021.
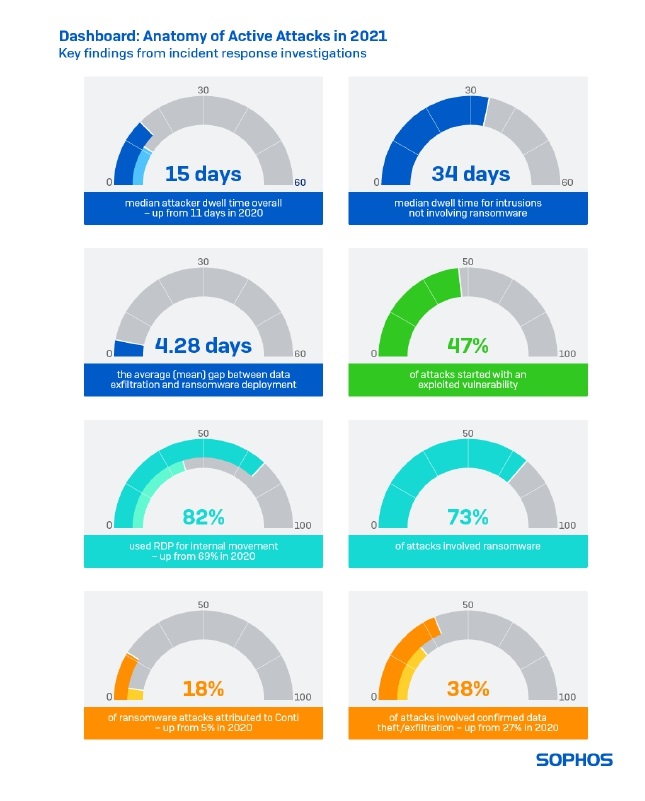
The findings show a 36% increase in attacker dwell time, with a median intruder dwell time of 15 days in 2021 versus 11 days in 2020.
The report also reveals the impact of ProxyShell vulnerabilities in Microsoft Exchange, which Sophos believes some Initial Access Brokers (IABs) leveraged to breach networks and then sell that access to other attackers.
“The world of cybercrime has become incredibly diverse and specialized. IABs have developed a cottage cybercrime industry by breaching a target, doing exploratory reconnaissance or installing a backdoor, and then selling the turn-key access to ransomware gangs for their own attacks,” said John Shier, senior security advisor at Sophos. “In this increasingly dynamic, specialty-based cyberthreat landscape, it can be hard for organizations to keep up with the ever-changing tools and approaches attackers use. It is vital that defenders understand what to look for at every stage of the attack chain, so they can detect and neutralize attacks as fast as possible.”
Sophos’ research also shows that intruder dwell time was longer in smaller organizations’ environments. Attackers lingered for approximately 51 days in organizations with up to 250 employees, while they typically spent 20 days in organizations with 3,000 to 5,000 employees.
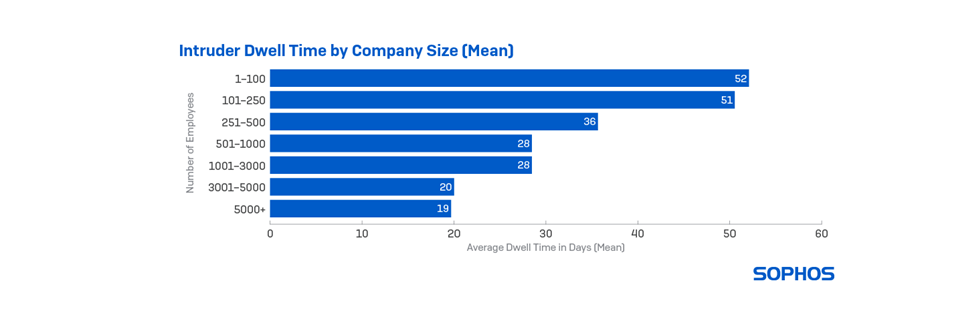

“Attackers consider larger organizations to be more valuable, so they are more motivated to get in, get what they want and get out. Smaller organizations have less perceived ‘value,’ so attackers can afford to lurk around the network in the background for a longer period. It’s also possible these attackers were less experienced and needed more time to figure out what to do once they were inside the network. Lastly, smaller organizations typically have less visibility along the attack chain to detect and eject attackers, prolonging their presence,” said Shier. “With opportunities from unpatched ProxyLogon and ProxyShell vulnerabilities and the uprise of IABs, we’re seeing more evidence of multiple attackers in a single target. If it’s crowded within a network, attackers will want to move fast to beat out their competition.”
Additional key findings in the playbook include:
- The median attacker dwell time before detection was longer for “stealth” intrusions that had not unfolded into a major attack such as ransomware, and for smaller organizations and industry sectors with fewer IT security resources. The median dwell time for organizations hit by ransomware was 11 days. For those that had been breached, but not yet affected by a major attack, such as ransomware (23% of all the incidents investigated), the median dwell time was 34 days. Organizations in the education sector or with fewer than 500 employees also had longer dwell times
- Longer dwell times and open entry points leave organizations vulnerable to multiple attackers. Forensic evidence uncovered instances where multiple adversaries, including IABs, ransomware gangs, cryptominers, and occasionally even multiple ransomware operators, were targeting the same organization simultaneously
- Despite a drop in using Remote Desktop Protocol (RDP) for external access, attackers increased their use of the tool for internal lateral movement. In 2020, attackers used RDP for external activity in 32% of the cases analyzed, but this decreased to 13% in 2021. While this shift is a welcome change and suggests organizations have improved their management of external attack surfaces, attackers are still abusing RDP for internal lateral movement. Sophos found that attackers used RDP for internal lateral movement in 82% of cases in 2021, up from 69% in 2020
- Common tool combinations used in attacks provide a powerful warning signal of intruder activity. For example, the incident investigations found that in 2021 PowerShell and malicious non-PowerShell scripts were seen together in 64% of cases; PowerShell and Cobalt Strike combined in 56% of cases; and PowerShell and PsExec were found in 51% of cases. The detection of such correlations can serve as an early warning of an impending attack or confirm the presence of an active attack
- Fifty percent of ransomware incidents involved confirmed data exfiltration – and with the available data, the mean gap between data theft and the deployment of ransomware was 4.28 days. Seventy-three percent of incidents Sophos responded to in 2021 involved ransomware. Of these ransomware incidents, 50% also involved data exfiltration. Data exfiltration is often the last stage of the attack before the release of the ransomware, and the incident investigations revealed the mean gap between them was 4.28 days and the median was 1.84 days
- Conti was the most prolific ransomware group seen in 2021, accounting for 18% of incidents overall. REvil ransomware accounted for one in 10 incidents, while other prevalent ransomware families included DarkSide, the RaaS behind the notorious attack on Colonial Pipeline in the U.S. and Black KingDom, one of the “new” ransomware families to appear in March 2021 in the wake of the ProxyLogon vulnerability. There were 41 different ransomware adversaries identified across the 144 incidents included in the analysis. Of these, around 28 were new groups first reported during 2021. Eighteen ransomware groups seen in incidents in 2020 had disappeared from the list in 2021
“The red flags that defenders should look out for include the detection of a legitimate tool, combination of tools, or activity in an unexpected place or at an uncommon time,” said Shier. “It is worth noting that there may also be times of little or no activity, but that doesn’t mean an organization hasn’t been breached. There are, for instance, likely to be many more ProxyLogon or ProxyShell breaches that are currently unknown, where web shells and backdoors have been implanted in targets for persistent access and are now sitting silently until that access is used or sold. Defenders need to be on the alert for any suspicious signals and investigate immediately. They need to patch critical bugs, especially those in widely used software, and, as a priority, harden the security of remote access services. Until exposed entry points are closed and everything that the attackers have done to establish and retain access is completely eradicated, just about anyone can walk in after them, and probably will.”

The Sophos Active Adversary Playbook 2022 is based on 144 incidents in 2021, targeting organizations of all sizes, in a wide range of industry sectors, and located in the U.S., Canada, the U.K., Germany, Italy, Spain, France, Switzerland, Belgium, Netherlands, Austria, the United Arab Emirates, Saudi Arabia, the Philippines, the Bahamas, Angola, and Japan. The most represented sectors are manufacturing (17%), followed by retail (14%), healthcare (13%), IT (9%), construction (8%), and education (6%).
The aim of Sophos’ report is help security teams understand what adversaries do during attacks and how to spot and defend against malicious activity on the network.
To learn more about attacker behaviors, tools and techniques, read the Sophos Active Adversary Playbook 2022 on Sophos News.
TechNews
NITDA DG Inaugurates National Technical Working Group on Cloud Infrastructure
REPORTER: Sandra Ani


In a significant move to bolster Nigeria’s digital infrastructure, the National Information Technology Development Agency (NITDA) has inaugurated the Technical Working Group (TWG) on National Cloud Infrastructure.
This initiative aims to enhance local cloud capabilities, attract hyper-scale investments, and position Nigeria as a leading technology hub in Africa.
Speaking at the inauguration, NITDA’s Director-General, Kashifu Inuwa, CCIE, emphasised the need for accurate data and regulatory frameworks to support these initiatives, necessary for Nigeria to control its digital infrastructure, data, and technological future noting that,
“Without this foundation, we cannot achieve true digital sovereignty. Our goal is to build an ecosystem where both local data centre providers can scale, and global hyper-scalers see Nigeria as a viable investment destination.”
While identifying lack of accurate data on Nigeria’s IT infrastructure as significant challenge, Inuwa noted that while Africa comprises nearly 19% of the world’s population, it hosts less than 1% of global data centres.
“This disparity, coupled with limited insights into Nigeria’s existing IT capacity, hampers investment efforts and without clear data on our infrastructure, attracting investment becomes challenging,” he said.
The NITDA boss maintained that, to address this, NITDA commissioned comprehensive research to assess Nigeria’s digital landscape which findings have highlighted the need for improved regulatory frameworks, clearer investment incentives, and stronger public-private collaboration. He added that subsequently upon this, NITDA has engaged global consultants to redefine strategies for cloud development.
As the TWG embarks on its mission, NITDA urges industry experts, policymakers, and stakeholders to contribute their expertise and resources. “With collective effort, Nigeria can emerge as the premier digital hub for West and Central Africa,” Inuwa concluded.
While corroborating the Director General’s point of views, Acting Director of Regulation and Compliance, Barrister Emmanuel Edet, underscored the importance of regulatory intervention in fostering a robust digital economy.
“Our objective is to establish policies and legal frameworks that support cloud development, enabling us to securely host and manage our data. This is crucial for the growth of our digital economy, he said.”
He also highlights the necessity of capacity building, stating that, “Equipping ourselves with top-tier training and expertise is essential to fully leverage digital technologies.” Barrister Edet called on all stakeholders to actively participate in shaping Nigeria’s digital future.
“Collaboratively, we must develop a framework that reflects our national interests, and it should be widely accepted. This effort will define Nigeria’s role in the global digital arena, he observed.
The TWG will help in the drive to attract hyperscale investments and enhance local cloud capabilities by proffering measures to encourage the use of accurate data, recommend the enactment and compliance to enabling policies.
Members of the TWG which includes Google, AWS, IBM, Oracle, Microsoft, HUAWEI Cloud, Equinix, Kasi, Rack Centre, Africa Data Centres, several other data centre operators and the Nigeria Data Protection Commission expressed support and readiness to volunteer and contribute resources.


…Nearly 80% of Organizations Hit by Ransomware Took More than a Week to Recover
Sophos, a global leader of innovative security solutions for defeating cyberattacks, today released a sector survey report, “The State of Ransomware in Healthcare 2024,” which revealed that the rate of ransomware attacks against healthcare organizations has reached a four-year high since 2021.
Of those organizations surveyed, two-thirds (67%) were impacted by ransomware attacks in the past year, up from 60% in 2023.
The rising rate of ransomware attacks against healthcare institutions contrasts with the declining rate of ransomware attacks across sectors; the overall rate of ransomware attacks fell from 66% in 2023 to 59% in 2024.
Alongside an increase in the rate of ransomware attacks, the healthcare sector reported increasingly longer recovery times.
Only 22% of ransomware victims fully recovered in a week or less, a considerable drop from the 47% reported in 2023 and 54% in 2022.
In addition, 37% took more than a month to recover, up from 28% in 2023, reflecting the increased severity and complexity of attacks.
“While we’ve seen the rate of ransomware attacks reach a kind of “homeostasis” or even decline across industries, attacks against healthcare organizations continue to intensify, both in number and scope. The highly sensitive nature of healthcare information and need for accessibility will always place a bullseye on the healthcare industry from cybercriminals. Unfortunately, cybercriminals have learned that few healthcare organizations are prepared to respond to these attacks, demonstrated by increasingly longer recovery times. These attacks can have immense ripple effects, as we’ve seen this year with major ransomware attacks impacting the healthcare industry and impacting patient care,” said John Shier, field CTO, Sophos.
“To combat these determined adversaries, healthcare organizations must adopt a more proactive, human-led approach to threat detection and response, combining advanced technology with continuous monitoring to stay ahead of attackers.”
Additional findings from the report include:
· Ransom Recovery Costs Surge: The mean cost of recovery in a healthcare ransomware attack was $2.57 million in 2024, up from $2.2 million in 2023 and double the 2021 cost
· Ransom Demands vs Payments: 57% of healthcare institutions that paid the ransom ended up paying more than the original demand
· Root Cause of Attack: Compromised credentials and exploited vulnerabilities were tied for the number one root cause of attack, each accounting for 34% of attacks
· Backups Targeted: 95% of healthcare organizations hit by ransomware in the past year said that cybercriminals attempted to compromise their backups during the attack.
· Increased Pressure: Organizations whose backups were compromised were more than twice as likely to pay the ransom to recover encrypted data (63% vs. 27%)
· Who Pays the Ransom: Insurance providers are heavily involved in ransom payments, contributing in 77% of cases. 19% of total ransom payment funding comes from insurance providers
The latest Sophos report on real-world ransomware experiences explores the full victim journey, from attack rate and root cause to operational impact and business outcomes, of 402 healthcare organizations.
The results for this sector survey report are part of a broader, vendor-agnostic survey of 5,000 cybersecurity/IT leaders conducted between January and February 2024 across 14 countries and 15 industry sectors.


Boxes have a multitude of uses, and the word “box”, lends itself to diverse contexts. For “Ajala Travelers,” the box is a necessity for keeping goods for their endless journeys. In literature, idiomatically, it can be said that “one has been boxed into a corner;” another might say to deal with a conundrum: “think outside the box;” then there is the “Pandora’s box” that no one wants opened.
To “box one’s ear’s” refers to a hit on the head, especially around one’s ears. For those who celebrate Christmas, “Boxing Day,” which is the 26th of December, the second day of Christmastide is not to be joked with: A day to unbox gifts. So much for the box.
Another type of boxes exists in the telecommunications world: The SIM Box. Have you ever received an international call but saw a local phone number ring in? That is SIM Boxing in action. Let me explain.
SIM boxing happens when a person uses a special equipment, what is called a SIM Box containing tens to hundreds of SIM Cards—from 32, to 96, to 512 and more SIMs —to terminate international calls by bringing in the international call into the SIM Box using internet connections and regenerating the calls to the called party from one of the hundred SIMs in the box.
This way, the called party will see the local number of the SIM from the SIM Box, and not the original international number calling.
With SIM Boxes, the syndicate charges international call carriers lower rates than what regular Nigerian telecommunications operators would charge, as they do not have to pay the full cost of maintaining and operating a phone network.
Basically, they are bypassing the normal route for international phone call termination to terminate international calls cheaply and making windfall profits off it.
Take for instance, a telecommunications operator in Nigeria would ordinarily charge international carriers 10cents per minute for terminating an international call in Nigeria. However, by routing the call through a SIM Boxing syndicate, the international telecommunications carrier only pays a fraction of the charge to the syndicate, say 5cents per minute and does not have to pay the full 10cents per minute charge.
The SIM Boxer will terminate this call to the called subscriber at a rate of, say N15 per minute using one of the SIM cards in their SIM Box. The SIM Boxer thus makes a killing from the differential between the rate charged to the international carrier and the rate paid to telecommunications operators whose SIM they utilise in their SIM Boxes, at the expense of our national security and income of mobile network operators and quality of our service to consumers.
Asides the revenue loss that local mobile network operators suffer courtesy the activities of these syndicates, networks face congestion around areas where the illegal call routings via SIM Boxing occurs. With the huge traffic from the boxes, callers around the area see more dropped calls, poor call quality, and slower data speeds.
The introduction of the linking of National Identity Numbers (NIN) to SIMs is one way the Federal Government has worked to tackle this criminal enterprise. With every SIM in the country being linked to an NIN, an identity is tied to the owner of each line, and regulators now have visibility of ownership. That is not all. There is also the “Max-4 Rule” where a subscriber is not allowed to have more than four lines per network operator linked to his NIN. With this rule in place, coupled with the NIN-SIM Linkage, every telephone subscriber in Nigeria would not just be accurately identifiable but limited to having only four telephone lines per subscriber.
To enforce this rule, the Nigerian Communications Commission (NCC) on the 29th of March 2024 announced the deadline for Mobile Network Operators to bar all subscribers who had five lines and above, and whose NIN failed the verification test of biometrics matching.
Over the last few weeks, sources within the NCC have confirmed cases where a single NIN was linked to over 100,000 lines.
Some NINs had well over 10,000 SIMS linked to them, others over a thousand, others had hundreds. Many have questioned the reports and asked, what would any single reasonable person be doing with these number of lines? Justifiable questions, because no sane person—who is not running a business—should own more than five SIM cards.
Given the ‘Max 4 Rule’ in place and the NIN-SIM Linkage Policy, SIM Boxers have been boxed into a corner.
The applications they use require tens to thousands of SIM Cards, and the imperative to stay anonymous. If these policies are well and fully implemented, this is the death knell for SIM Boxing merchants.
But the regulator, NCC needs to be fast and ready for the battle ahead. SIM Boxing is a billion-dollar criminal enterprise. They are not going to go down without a fight. It is like taking a bone being chewed from the mouth of a bulldog.
Already, the battle seems to have kicked off. A lawyer, Barrister Olukoya Ogunbeje has recently taken the Federal Government, NCC and Mobile Network Operators to court, claiming that the barring of SIMs not linked to NINs goes against his fundamental human rights, and has cost him the loss of business opportunities.
Anyone who has Nigeria’s interest at heart ordinarily supports this policy. It then does not add up seeing a so-called activist lawyer take up such a matter that is clearly against the public interest—unless this is the Haka cry of SIM Boxers.
A most interesting observation with his case is that it is not even a class action, but individually driven. It begs the question then, who is funding Barr. Olukoya Ogungbeje? What is his interest in fighting this policy that puts paid to the business of a criminal enterprise? Is he funded by interests in the SIM Boxing world? Time would tell. But in the meantime, NCC must go head on without fear or intimation and clean the Augean stable of SIM ownership in Nigeria.
Suleiman Bala Bakori is a researcher, and writes from the FCT.










