TechNews
Sophos’ Active Adversary Playbook 2022 Reveals Attacker Dwell Time Increased by 36%
Increase attributed to exploitation of ProxyLogon and ProxyShell vulnerabilities, plus initial access brokers


Sophos, a global leader in next-generation cybersecurity, today released the “Active Adversary Playbook 2022,” detailing attacker behaviors that Sophos’ Rapid Response team saw in the wild in 2021.
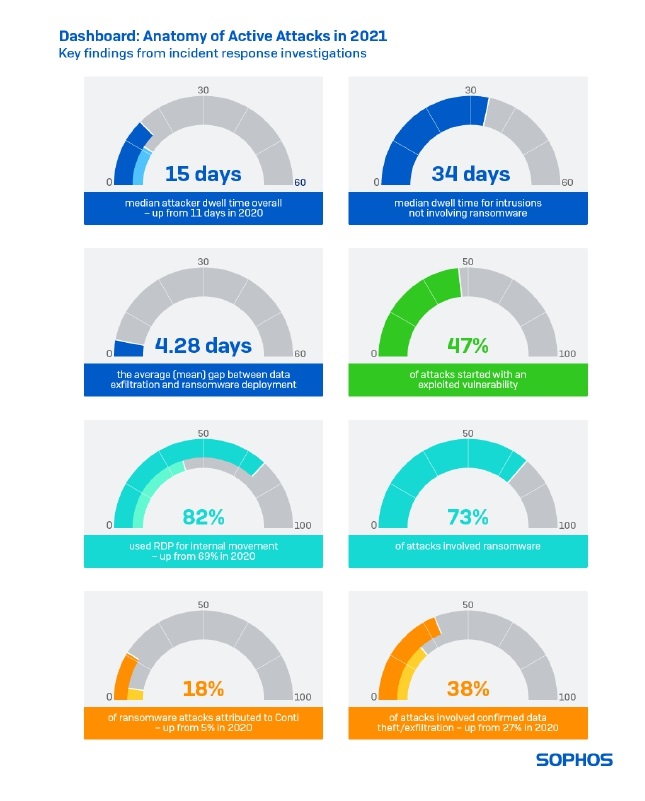
The findings show a 36% increase in attacker dwell time, with a median intruder dwell time of 15 days in 2021 versus 11 days in 2020.
The report also reveals the impact of ProxyShell vulnerabilities in Microsoft Exchange, which Sophos believes some Initial Access Brokers (IABs) leveraged to breach networks and then sell that access to other attackers.
“The world of cybercrime has become incredibly diverse and specialized. IABs have developed a cottage cybercrime industry by breaching a target, doing exploratory reconnaissance or installing a backdoor, and then selling the turn-key access to ransomware gangs for their own attacks,” said John Shier, senior security advisor at Sophos. “In this increasingly dynamic, specialty-based cyberthreat landscape, it can be hard for organizations to keep up with the ever-changing tools and approaches attackers use. It is vital that defenders understand what to look for at every stage of the attack chain, so they can detect and neutralize attacks as fast as possible.”
Sophos’ research also shows that intruder dwell time was longer in smaller organizations’ environments. Attackers lingered for approximately 51 days in organizations with up to 250 employees, while they typically spent 20 days in organizations with 3,000 to 5,000 employees.
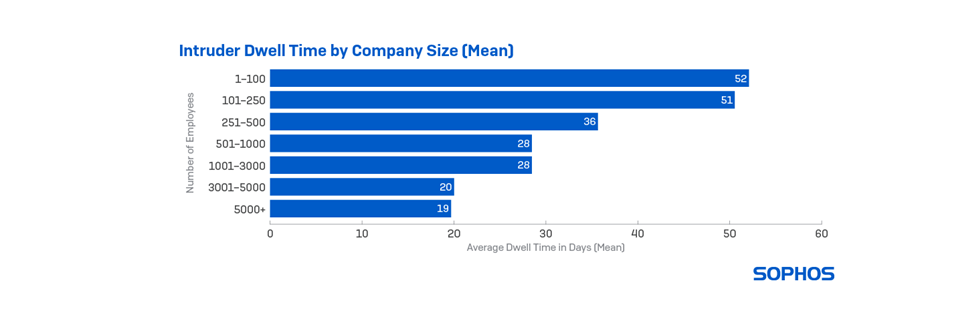

“Attackers consider larger organizations to be more valuable, so they are more motivated to get in, get what they want and get out. Smaller organizations have less perceived ‘value,’ so attackers can afford to lurk around the network in the background for a longer period. It’s also possible these attackers were less experienced and needed more time to figure out what to do once they were inside the network. Lastly, smaller organizations typically have less visibility along the attack chain to detect and eject attackers, prolonging their presence,” said Shier. “With opportunities from unpatched ProxyLogon and ProxyShell vulnerabilities and the uprise of IABs, we’re seeing more evidence of multiple attackers in a single target. If it’s crowded within a network, attackers will want to move fast to beat out their competition.”
Additional key findings in the playbook include:
- The median attacker dwell time before detection was longer for “stealth” intrusions that had not unfolded into a major attack such as ransomware, and for smaller organizations and industry sectors with fewer IT security resources. The median dwell time for organizations hit by ransomware was 11 days. For those that had been breached, but not yet affected by a major attack, such as ransomware (23% of all the incidents investigated), the median dwell time was 34 days. Organizations in the education sector or with fewer than 500 employees also had longer dwell times
- Longer dwell times and open entry points leave organizations vulnerable to multiple attackers. Forensic evidence uncovered instances where multiple adversaries, including IABs, ransomware gangs, cryptominers, and occasionally even multiple ransomware operators, were targeting the same organization simultaneously
- Despite a drop in using Remote Desktop Protocol (RDP) for external access, attackers increased their use of the tool for internal lateral movement. In 2020, attackers used RDP for external activity in 32% of the cases analyzed, but this decreased to 13% in 2021. While this shift is a welcome change and suggests organizations have improved their management of external attack surfaces, attackers are still abusing RDP for internal lateral movement. Sophos found that attackers used RDP for internal lateral movement in 82% of cases in 2021, up from 69% in 2020
- Common tool combinations used in attacks provide a powerful warning signal of intruder activity. For example, the incident investigations found that in 2021 PowerShell and malicious non-PowerShell scripts were seen together in 64% of cases; PowerShell and Cobalt Strike combined in 56% of cases; and PowerShell and PsExec were found in 51% of cases. The detection of such correlations can serve as an early warning of an impending attack or confirm the presence of an active attack
- Fifty percent of ransomware incidents involved confirmed data exfiltration – and with the available data, the mean gap between data theft and the deployment of ransomware was 4.28 days. Seventy-three percent of incidents Sophos responded to in 2021 involved ransomware. Of these ransomware incidents, 50% also involved data exfiltration. Data exfiltration is often the last stage of the attack before the release of the ransomware, and the incident investigations revealed the mean gap between them was 4.28 days and the median was 1.84 days
- Conti was the most prolific ransomware group seen in 2021, accounting for 18% of incidents overall. REvil ransomware accounted for one in 10 incidents, while other prevalent ransomware families included DarkSide, the RaaS behind the notorious attack on Colonial Pipeline in the U.S. and Black KingDom, one of the “new” ransomware families to appear in March 2021 in the wake of the ProxyLogon vulnerability. There were 41 different ransomware adversaries identified across the 144 incidents included in the analysis. Of these, around 28 were new groups first reported during 2021. Eighteen ransomware groups seen in incidents in 2020 had disappeared from the list in 2021
“The red flags that defenders should look out for include the detection of a legitimate tool, combination of tools, or activity in an unexpected place or at an uncommon time,” said Shier. “It is worth noting that there may also be times of little or no activity, but that doesn’t mean an organization hasn’t been breached. There are, for instance, likely to be many more ProxyLogon or ProxyShell breaches that are currently unknown, where web shells and backdoors have been implanted in targets for persistent access and are now sitting silently until that access is used or sold. Defenders need to be on the alert for any suspicious signals and investigate immediately. They need to patch critical bugs, especially those in widely used software, and, as a priority, harden the security of remote access services. Until exposed entry points are closed and everything that the attackers have done to establish and retain access is completely eradicated, just about anyone can walk in after them, and probably will.”

The Sophos Active Adversary Playbook 2022 is based on 144 incidents in 2021, targeting organizations of all sizes, in a wide range of industry sectors, and located in the U.S., Canada, the U.K., Germany, Italy, Spain, France, Switzerland, Belgium, Netherlands, Austria, the United Arab Emirates, Saudi Arabia, the Philippines, the Bahamas, Angola, and Japan. The most represented sectors are manufacturing (17%), followed by retail (14%), healthcare (13%), IT (9%), construction (8%), and education (6%).
The aim of Sophos’ report is help security teams understand what adversaries do during attacks and how to spot and defend against malicious activity on the network.
To learn more about attacker behaviors, tools and techniques, read the Sophos Active Adversary Playbook 2022 on Sophos News.









