TechNews
Sophos Details How Fake Apps on Apple’s App Store Are Used by Cybercriminals for CryptoRom Schemes
SANDRA ANI reporting


Sophos, a global leader in innovating and delivering cybersecurity as a service, today released new findings on CryptoRom scams—elaborate financial fraud schemes that prey on and trick dating app users into making fake cryptocurrency investments—in its latest report, “Fraudulent Trading Apps Sneak into Apple and Google App Stores.”
The report details the first fake CryptoRom apps —Ace Pro and MBM_BitScan— to successfully bypass Apple’s strict security protocols.
Previously, cybercriminals used workaround techniques to convince victims to download illegitimate iPhone apps that were not sanctioned by the Apple App Store.
Sophos immediately notified Apple and Google; both have since removed the fraudulent apps from their respective stores.


“In general, it’s hard to get malware past the security review process in the Apple App Store. That’s why, when we originally began investigating CryptoRom scams targeting iOS users, the scammers would have to persuade users to first install a configuration profile before they could install the fake trading app. This obviously involves an additional level of social engineering—a level that’s hard to surmount. Many potential victims would be ‘alerted’ that something wasn’t right when they couldn’t directly download a supposedly legitimate app. By getting an application onto the App Store, the scammers have vastly increased their potential victim pool, particularly since most users inherently trust Apple,” said Jagadeesh Chandraiah, senior threat researcher, Sophos. “Both apps are also not affected by iOS’ new Lockdown mode, which prevents scammers from loading mobile profiles helpful for social engineering. In fact, these CryptoRom scammers may be shifting their tactics—i.e., focusing on bypassing the App Store review process—in light of the security features in Lockdown.”
To lure the victim who was conned with Ace Pro, for instance, the scammers created and actively maintained a fake Facebook profile and persona of a woman supposedly living a lavish lifestyle in London.
After building a rapport with the victim, the scammers suggested the victim download the fraudulent Ace Pro app and the cryptocurrency fraud unfolded from there.
Ace Pro is described in the app store as a QR code scanner but is a fraudulent crypto trading platform. Once opened, users see a trading interface where they can supposedly deposit and withdraw currency. However, any money deposited goes directly to the scammers.
In order to get past App Store security, Sophos believes the scammers had the app connect to a remote website with benign functionality when it was originally submitted for review.
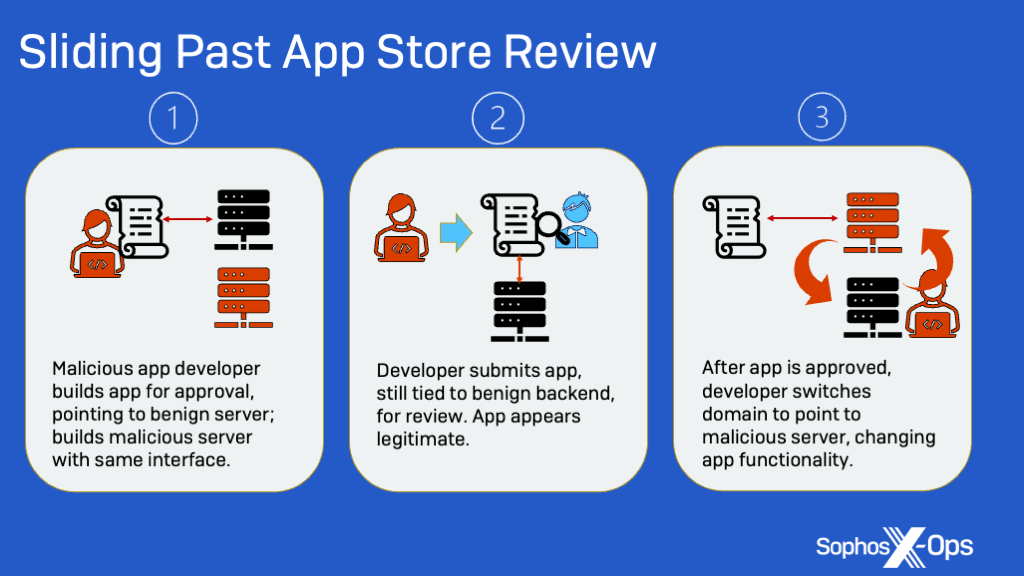

The domain included code for QR scanning to make it look legitimate to app reviewers. However, once the app was approved, the scammers redirected the app to an Asian-registered domain. This domain sends a request that responds with content from another host that ultimately delivers the fake trading interface.
MBM_BitScan is also an app for Android, but it is known as BitScan on Google Play. The two apps communicate with the same Command and Control (C2) infrastructure; this C2 infrastructure then communicates with a server that resembles a legitimate Japanese crypto firm. Everything else that is malicious is handled in a web interface, which is why it is hard for Google Play’s code reviewers to detect it as fraudulent.
CryptoRom, a subset of family of scams known as sha zhu pan (杀猪盘)—literally “pig butchering plate”—is a well-organized, syndicated scam operation that uses a combination of romance-centered social engineering and fraudulent crypto trading applications and websites to lure victims and steal their money after gaining their confidence. Sophos has been tracking and reporting on these scams that reap millions of dollars for two years.
Learn more about the criminals behind the CryptoRom rings and these fraudulent apps in “Fraudulent CryptoRom Trading Apps Sneak into Apple and Google App Stores” on Sophos.com.
-



 News4 days ago
News4 days ago‘You escape, or you die’: African men say Russia duped them into fighting in Ukraine
-



 Hospitality2 days ago
Hospitality2 days agoThe Nature Conservancy and FSC Africa Sign Strategic Partnership to Strengthen Sustainable Forest Management Across Africa
-



 Transport2 days ago
Transport2 days agoAkin Fadeyi Foundation unveils new advocacy campaign to curb road accidents
-



 Energy2 days ago
Energy2 days agoPayment Security Remains Biggest Barrier to Bankable Gas and Power Projects — FirstCap MD






